科林克拉克 2021年8月6日

美国海军少将 David Furness 和 Mandiant 高级副总裁 Ron Bushar
华盛顿消息:“如果要我判断谁会在现在的网络空间胜利?我不认为答案是肯定的,对很多人来说,就是这样?”这是Mandiant的高级副总裁兼首席技术官Ron Bushar在本周的海空会议上向观众发表的演讲,他说的并没有错。
“不幸的事实是,”Ron Bushar继续说,“网络攻击的速度、频率、强度和影响在过去几年中都只是增加了。”
这些“正在迅速超越我们的创新能力、防御网络工具、武器和漏洞的能力,这些都是同样的问题,对吧?随着我们加速技术、创新我们和软件开发,我们无法跟上任何地方”看到的代码中的人为错误。”
Ron Bushar认为答案不是更多的网络防御,那只是建立很高很高的网络墙,(作用不大)。
“我们在守望,”他说。“我认为我们在这个领域还没有真正的威慑。这将是我们思考未来可能的关键。”
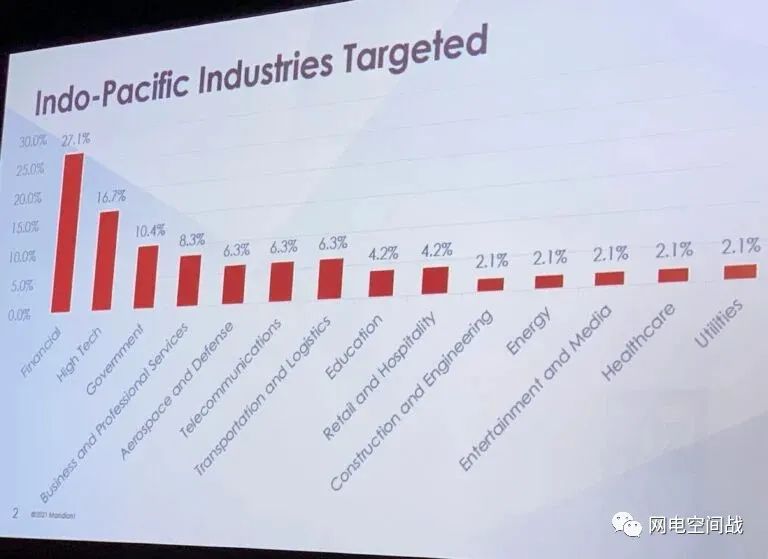
网络事件图表 SeaAirSpace 2021 图片来源:Mandiant
他在周一下午对听众说,追求一种“除了点名和羞辱之外没有任何真正的威慑合作”的主要外交战略可能长期有效。
Ron Bushar认为,美国未来几年前就应该达到这样的地步:“我们必须采用独特的模式,让我们在网络高墙之上更上一层楼,吧?让游戏进入我们的环境。”
当你真正了解如何被阻止、被他人利用或小偷使用网络工具攻击你的系统或将劫持为人质时,一切就会变得更加复杂。美国的能力必须尽可能升级。但Ron Bushar明确表示,网络墙的防御能力确实很强。但网络归因和威慑比网络防御更重要
“我们只是正在防御,”Mandiant 高级副总裁 Ron Bushar 说。“我认为我们在这个领域还没有达到真正的威慑水平。这将是思考我们未来几年战略的关键。”
Mandiant CTO: Cyber Attribution, Deterrence More Vital Than Defense
"We"re on the defense," Ron Bushar, senior vice president at Mandiant says. "I don"t think we"ve hit a real deterrence level in this space yet. And that"s going to be key to thinking through our strategy over the next few years."
By COLIN CLARKon August 06, 2021 at 7:37 AM
Marine Maj. Gen. David Furness and Ron Bushar, senior vice president of Mandiant.
WASHINGTON: “If I ask for a show of hands, who thinks we’re winning in cyberspace these days? I don’t think the answer is yes, for many folks. Right?”
That was Ron Bushar, senior vice president and CTO of Mandiant, speaking to an audience at this week’s Sea Air Space conference. And he wasn’t wrong — in a room full of military professionals, there wasn’t a lot of pushback to his query.
“The unfortunate truth,” Bushar continued, “is both the pace, the frequency, the intensity, and the impact of cyber attacks have only increased over the past several years.”
These attacks are “rapidly outpacing our ability to innovate, defend against cyber tools and weapons and vulnerabilities that are the same problem, right? As we accelerate technology, innovation, and software development, we can’t keep up with the human mistakes that get put into code everywhere we see it.”
The answer, Bushar said, is NOT more defense, what he called higher and higher cyber walls.
“We’re on the defense,” he said. “I don’t think we’ve hit a real deterrence level in this space yet. And that’s going to be key to thinking through our strategy over the next few years.”
Cyber incident chart SeaAirSpace 2021 Credit: Mandiant
Pursuing a primarily diplomatic strategy that “doesn’t have any real deterrence mechanisms built into it beyond kind of naming and shaming” is unlikely to be effective over the long haul, he told the audience on Monday afternoon.
Instead, the US and its allies “have to think about attribution as a strategic imperative, not just as a nice-to-have,” he said. He acknowledged many would “argue that it’s impossible to get good attribution in this space,” but, to provide deterrence “we have to get better at it.”
That led Bushar to a place many observers think the US federal government should have reached several years ago: “We have to get away from this model of, let’s go higher with cyber walls, right? Let’s deter our adversaries or prevent our adversaries from getting into our environments.”
Of course, when you get to the nitty-gritty of just how to deter an enemy or competitor or thief from using cyber tools to attack your systems or hold them hostage everything suddenly gets much more complicated. If the US counterattacks, then the country or group that struck will know more about American capabilities and may escalate. But Bushar made clear the castle wall defense really isn’t working.
声明:本文来自网电空间战,版权归作者所有。文章内容仅代表作者独立观点,不代表安全内参立场,转载目的在于传递更多信息。如有侵权,请联系 anquanneican@163.com。
