随着人们安全意识的提高,安全传递秘密信息逐渐成为公众的需求。隐写术是一种在另一个载体中表示秘密信息的技术,目的是在不引起怀疑的情况下传输秘密信息。大多数传统的隐写算法通过修改统计特征来隐藏秘密信息,这会给载体留下痕迹。虽然这些修改很小,人眼无法区分,但它们可以通过隐写分析算法检测到。不同的是,无载体隐写术通过构造秘密信息与载体之间的关系来完成信息隐藏的过程。由于没有对载体进行任何修改,所有的隐写析算法都将失效。本文包括了90多篇关于无载体隐写算法的综述,介绍了无载体图像和视频隐写算法的主要发展过程。总结了现有方法的主要贡献。此外,本文还对当前图像算法和视频算法的容量、鲁棒性和安全性等一般问题进行了充分的讨论。
现存的基于图像的无载体隐写方法主要分为两种,基于映射式无载体图像隐写方法和基于生成式的无载体图像隐写方法,而基于视频的无载体隐写方法集中于映射式。
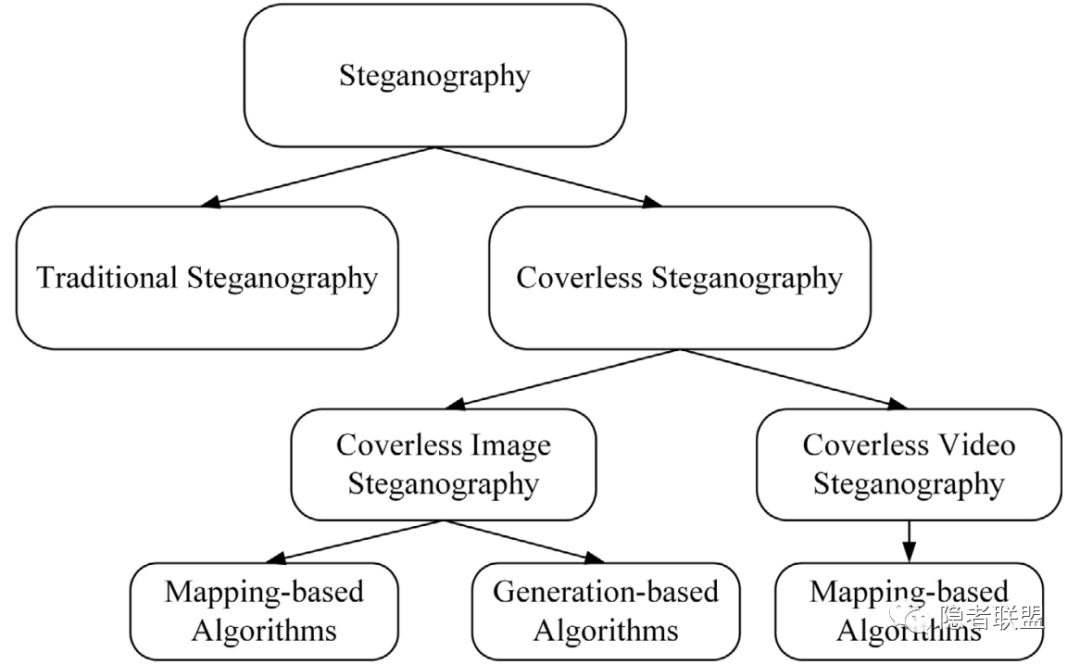
下面的时间线整理了一些典型的无载体隐写方法。
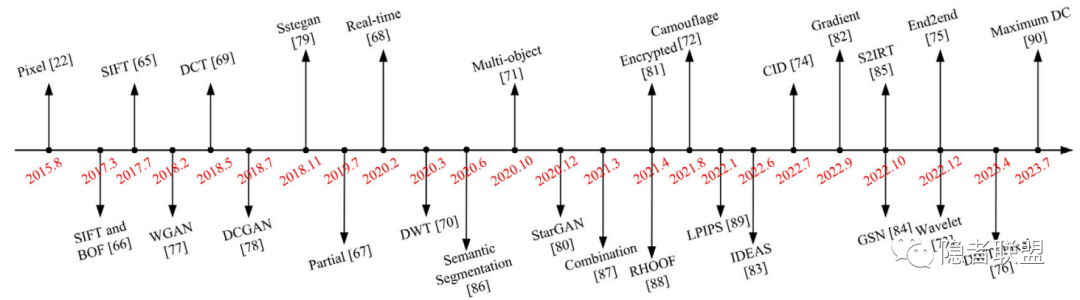
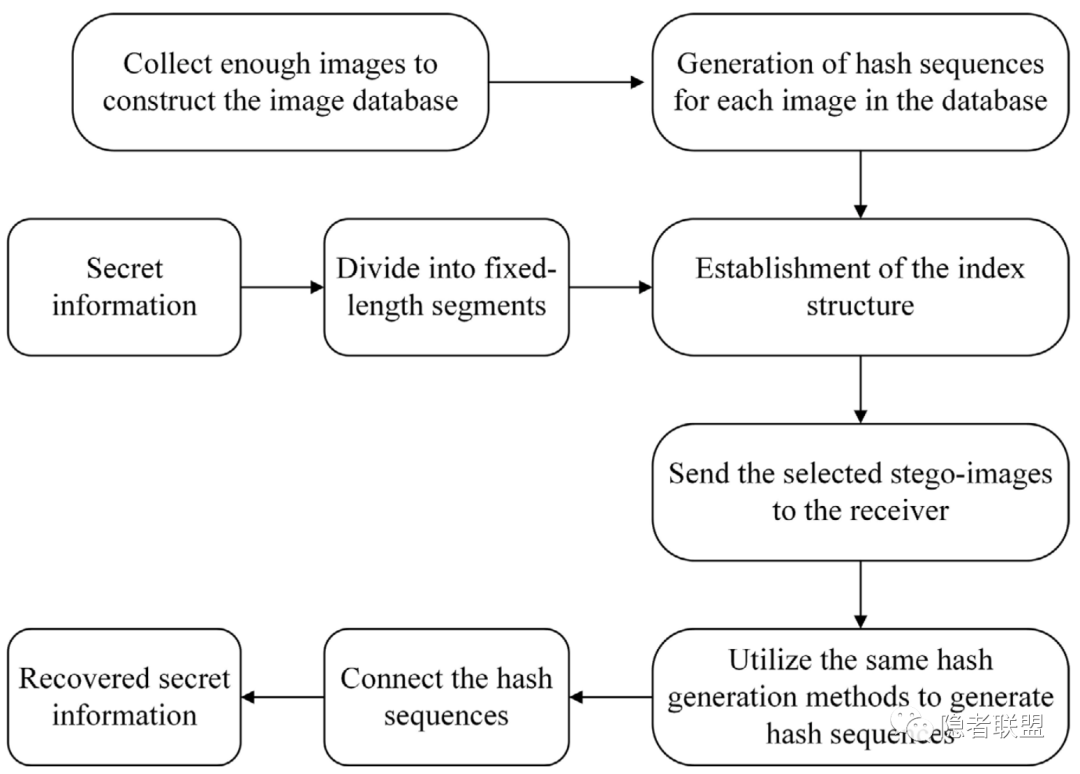
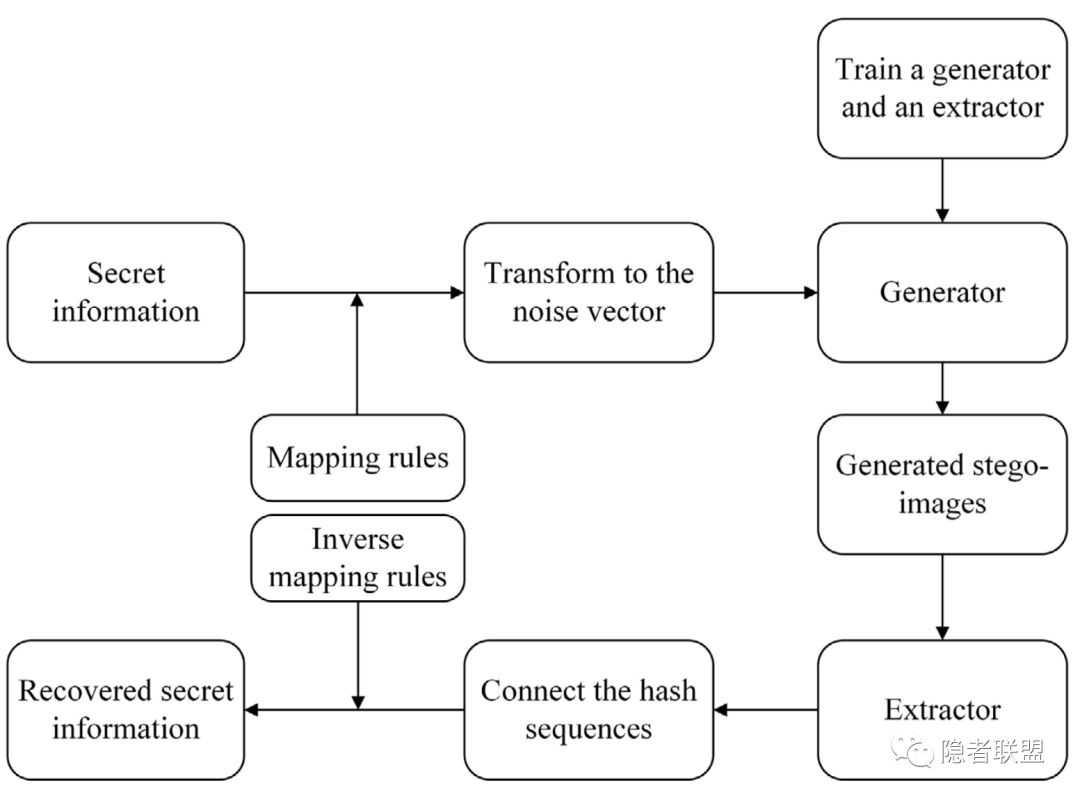
下面两张图分别总结了基于映射式和基于生成式方法的通用流程:
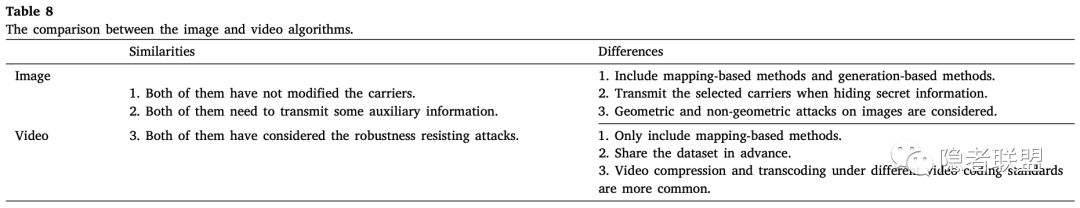
下表列出了基于图像和基于视频的无载体隐写方法之间的相似性和不同之处:
此外,本文还分别从容量、鲁棒性、安全性角度分析了现有的图像算法和视频算法存在的优势和缺陷。
参考文献
[22] Z. Zhou, H. Sun, R. Harit, X. Chen, X. Sun, Coverless image steganography without embedding, in: International Conference on Cloud Computing and Security, Springer, 2015, pp. 123–132.
[65] S. Zheng, L. Wang, B. Ling, D. Hu, Coverless information hiding based on robust image hashing, in: International Conference on Intelligent Computing, Springer, 2017, pp. 536–547.
[66] C. Yuan, Z. Xia, X. Sun, Coverless image steganography based on SIFT and BOF, J. Internet Technol. 18 (2) (2017) 435–442.
[67] Z. Zhou, Y. Mu, Q. Wu, Coverless image steganography using partial-duplicate image retrieval, Soft Comput. 23 (13) (2019) 4927–4938.
[68] Y. Luo, J. Qin, X. Xiang, Y. Tan, Q. Liu, L. Xiang, Coverless real-time image information hiding based on image block matching and dense convolutional network, J. Real-Time Image Process. 17 (1) (2020) 125–135.
[69] X. Zhang, F. Peng, M. Long, Robust coverless image steganography based on DCT and LDA topic classification, IEEE Trans. Multimed. 20 (12) (2018) 3223–3238.
[70] Q. Liu, X. Xiang, J. Qin, Y. Tan, J. Tan, Y. Luo, Coverless steganography based on image retrieval of DenseNet features and DWT sequence mapping, Knowl.-Based Syst. 192 (2020) 105375.
[71] Y. Luo, J. Qin, X. Xiang, Y. Tan, Coverless image steganography based on multi-object recognition, IEEE Trans. Circuits Syst. Video Technol. 31 (7) (2020) 2779–2791.
[72] Q. Liu, X. Xiang, J. Qin, Y. Tan, Q. Zhang, A robust coverless steganography scheme using camouflage image, IEEE Trans. Circuits Syst. Video Technol. 32 (6) (2021) 4038–4051.
[73] N.A. Karim, S.A. Ali, M.J. Jawad, A coverless image steganography based on robust image wavelet hashing, TELKOMNIKA (Telecommun. Comput. Electron. Control) 20 (6) (2022) 1317–1325.
[74] L. Zou, J. Li, W. Wan, Q.J. Wu, J. Sun, Robust coverless image steganography based on neglected coverless image dataset construction, IEEE Trans. Multimed. (2022) 1–13.
[75] L. Meng, X. Jiang, Z. Zhang, Z. Li, T. Sun, A robust coverless image steganography based on an end-to-end hash generation model, IEEE Trans. Circuits Syst. Video Technol. 33 (7) (2022) 3542–3558.
[76] S. Biswas, S. Debnath, R.K. Mohapatra, Coverless image steganography based on DWT approximation and pixel intensity averaging, in: 2023 7th International Conference on Trends in Electronics and Informatics (ICOEI), IEEE, 2023, pp. 1554–1561.
[77] X. Duan, H. Song, Coverless information hiding based on generative model, 2018, arXiv preprint arXiv:1802.03528.
[78] D. Hu, L. Wang, W. Jiang, S. Zheng, B. Li, A novel image steganography method via deep convolutional generative adversarial networks, IEEE Access 6 (2018) 38303–38314.
[79] Z. Wang, N. Gao, X. Wang, X. Qu, L. Li, SSteGAN: Self-learning steganography based on generative adversarial networks, in: International Conference on Neural Information Processing, Springer, 2018, pp. 253–264.
[80] X. Chen, Z. Zhang, A. Qiu, Z. Xia, N. Xiong, A novel coverless steganography method based on image selection and StarGAN, IEEE Trans. Netw. Sci. Eng. 9 (1) (2022) 219–230.
[81] Q. Li, X. Wang, X. Wang, B. Ma, C. Wang, Y. Shi, An encrypted coverless information hiding method based on generative models, Inform. Sci. 553 (2021) 19–30.
[82] F. Peng, G. Chen, M. Long, A robust coverless steganography based on generative adversarial networks and gradient descent approximation, IEEE Trans. Circuits Syst. Video Technol. 32 (9) (2022) 5817–5829.
[83] X. Liu, Z. Ma, J. Ma, J. Zhang, G. Schaefer, H. Fang, Image disentanglement autoencoder for steganography without embedding, in: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, 2022, pp. 2303–2312.
[84] P. Wei, S. Li, X. Zhang, G. Luo, Z. Qian, Q. Zhou, Generative steganography network, in: Proceedings of the 30th ACM International Conference on Multimedia, 2022, pp. 1621–1629.
[85] Z. Zhou, Y. Su, J. Li, K. Yu, Q.J. Wu, Z. Fu, Y. Shi, Secret-to-image reversible transformation for generative steganography, IEEE Trans. Dependable Secure Comput. (2022) 1–17.
[86] N. Pan, J. Qin, Y. Tan, X. Xiang, G. Hou, A video coverless information hiding algorithm based on semantic segmentation, EURASIP J. Image Video Process. 2020 (1) (2020) 1–18.
[87] L. Zou, W. Wan, B. Wei, J. Sun, Coverless video steganography based on inter frame combination, in: International Symposium on Geometry and Vision, Springer, 2021, pp. 134–141.
[88] Y. Tan, J. Qin, X. Xiang, C. Zhang, Z. Wang, Coverless steganography based on motion analysis of video, Secur. Commun. Netw. 2021 (2021) 1–16.
[89] R. Li, J. Qin, Y. Tan, N.N. Xiong, Coverless video steganography based on frame sequence perceptual distance mapping, Comput. Mater. Contin. 73 (1) (2022) 1571–1583.
[90] L. Meng, X. Jiang, Z. Zhang, Z. Li, T. Sun, A robust coverless video steganography based on maximum DC coefficients against video attacks, Multimedia Tools Appl. (2023) 1–35.
论文信息
相关论文已发表于Neurocomputing期刊,作者为上海交通大学网络空间安全学院信息安全与认知实验室的孟来锦、蒋兴浩教授和孙锬锋教授。
lL. Meng, X. Jiang, and T. Sun, "A Review of Coverless Steganography," Neurocomputing, v 566, January 21, 2024, doi: 10.1016/j.neucom.2023.126945.
供稿:蒋兴浩、孙锬锋,上海交通大学网络空间安全学院“信息安全与认知实验室”
💡招聘信息:本实验室长期招收数字媒体对抗/攻击及取证技术、大语言模型安全检测技术、多模态音视频分析技术的博士后、青年教师、副高青年教授等,欢迎联系孙锬锋教授,TEL:13564454752.
声明:本文来自隐者联盟,版权归作者所有。文章内容仅代表作者独立观点,不代表安全内参立场,转载目的在于传递更多信息。如有侵权,请联系 anquanneican@163.com。
